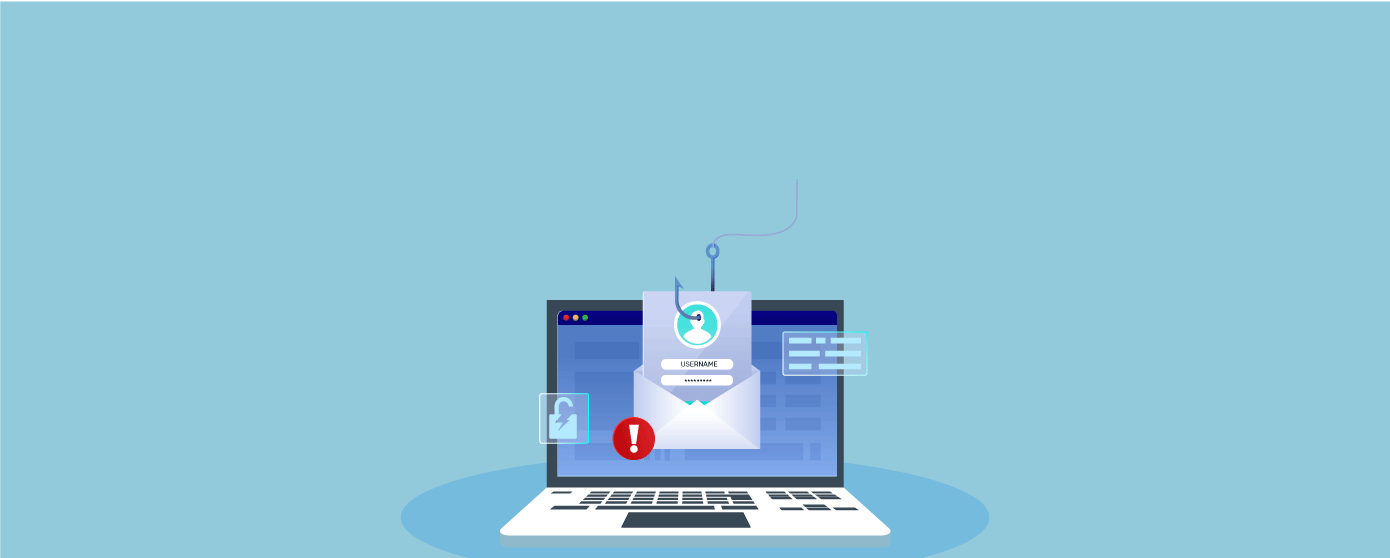
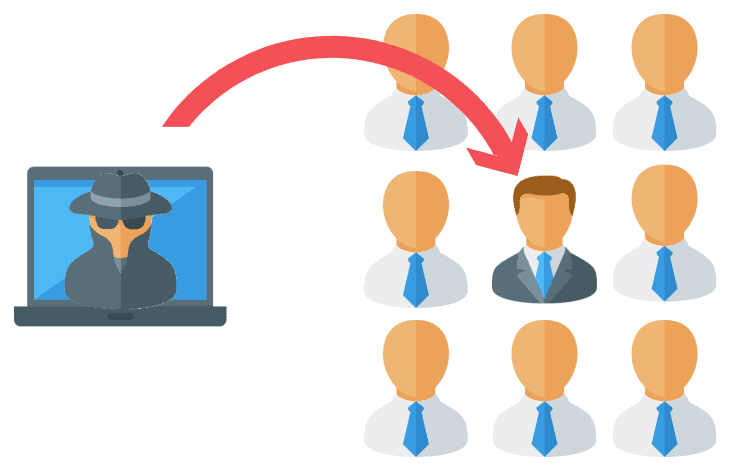
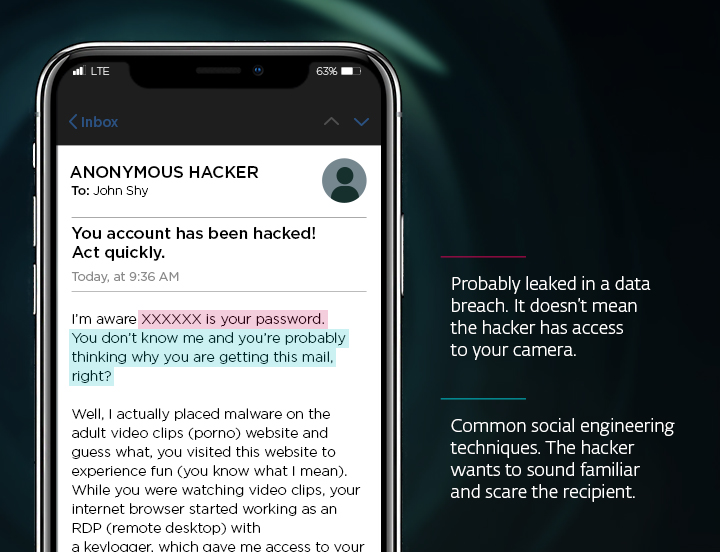
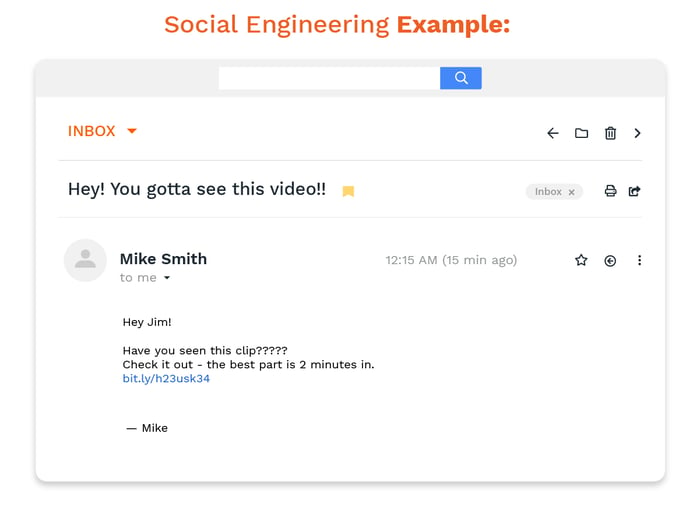
Phishing Stock Footage and Videos. 1,532 Phishing royalty free video and movie clips available to search from hundreds of buyout footage producers.

Social Media Video Marketing 101: Your Ultimate Guide to Video Strategy for Social Media | Vimeo Blog

St Joseph's Engineering College students dance wearing burqa in Mangaluru, suspended after video goes viral | India News | Zee News